
ACF Security Architecture
At ACF, we prioritize security at every layer of our platform to ensure the integrity, privacy, and confidentiality of your sensitive data and communications. Our security framework incorporates industry-leading practices, cutting-edge technologies, and privacy-enhancing tools to offer a robust defense against potential threats. Here’s how ACF integrates and implements top-tier security measures:
1. Secure Communication
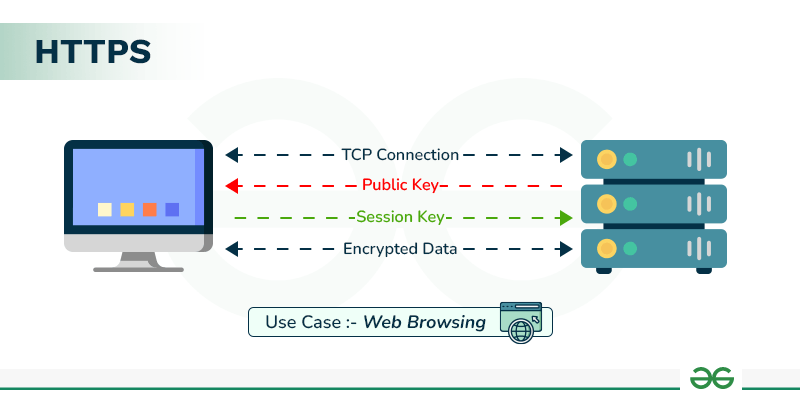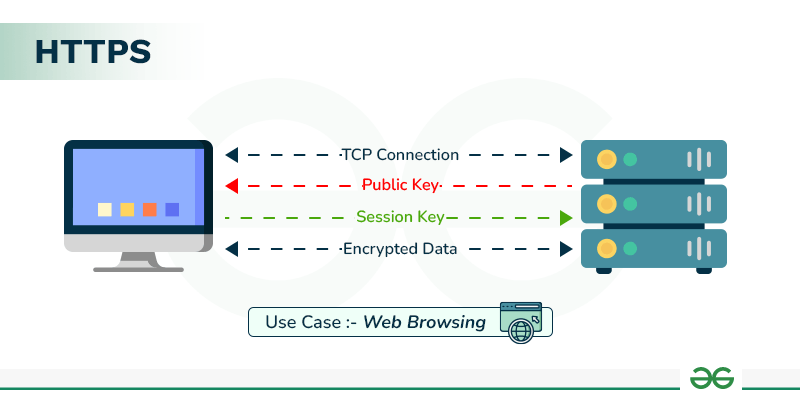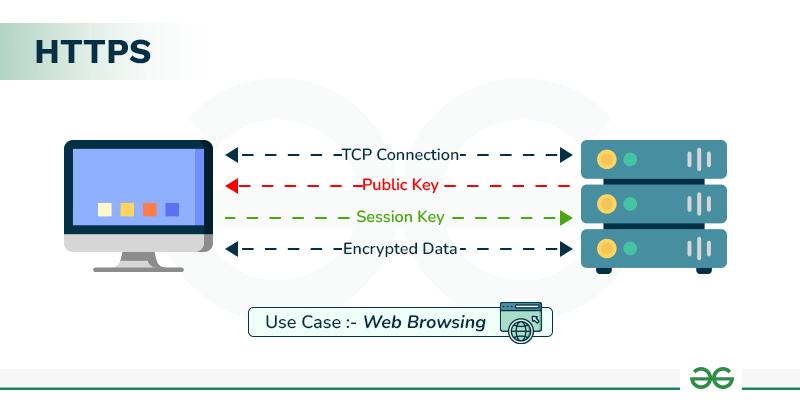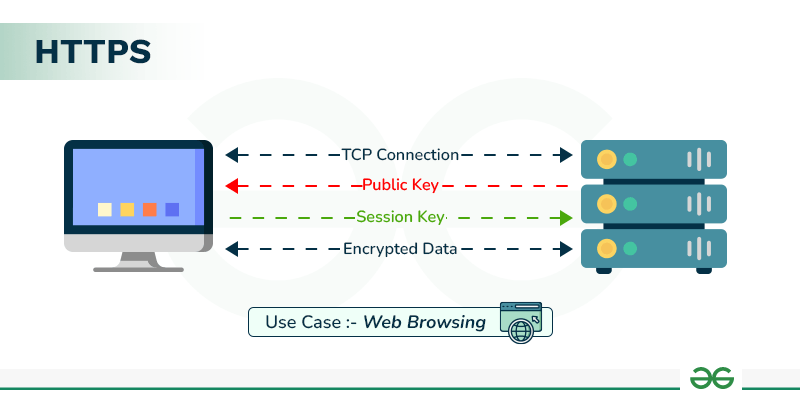
ACF ensures that all data exchanged between the platform and our APIs is protected with strong encryption protocols.
Tor-based Anonymized Communication: We enhance user privacy by routing traffic through the Tor network, effectively anonymizing data and masking user identities.
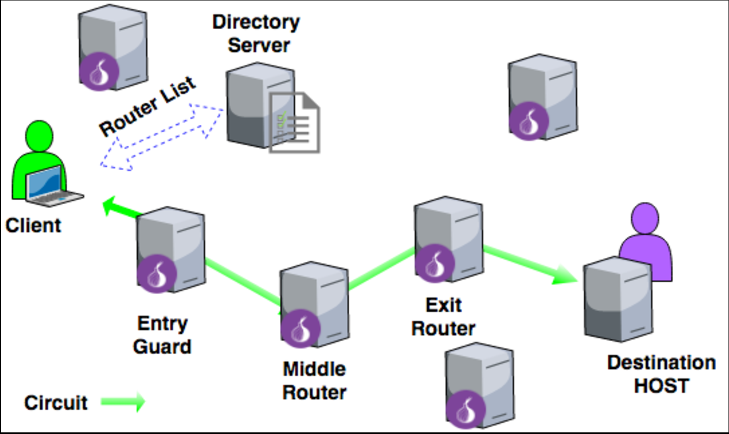
Requests from the mobile platform: These are routed through Tor’s SOCKS5 proxy, ensuring that user IP addresses are protected from exposure.
Tor Hidden Service API: By configuring the API as a Tor hidden service (with a unique .onion address), only users connected to the Tor network can access the API, preventing unwanted exposure to the open internet.
HTTPS Protocol: To bolster the security of data in transit, HTTPS (SSL/TLS) is enforced across all communications, ensuring that all data exchanged is encrypted end-to-end.
2. Data Protection and Storage
ACF adopts advanced techniques to safeguard data both at rest and in transit, ensuring that your sensitive information remains secure from unauthorized access.
End-to-End Encryption: All communications with our APIs are encrypted using AES 256-bit encryption. Sensitive data, such as user credentials, payment information, and personal details, is protected with strong encryption algorithms. Even if data were to be intercepted, the encryption ensures it remains unreadable without the appropriate decryption keys.
Decentralized Web3 Storage: We do not store data in a centralized location. Instead, ACF leverages Web3 decentralized storage, ensuring high fault tolerance and distributed networks. This approach eliminates single points of failure and enhances data resilience, keeping your information safe from potential breaches.
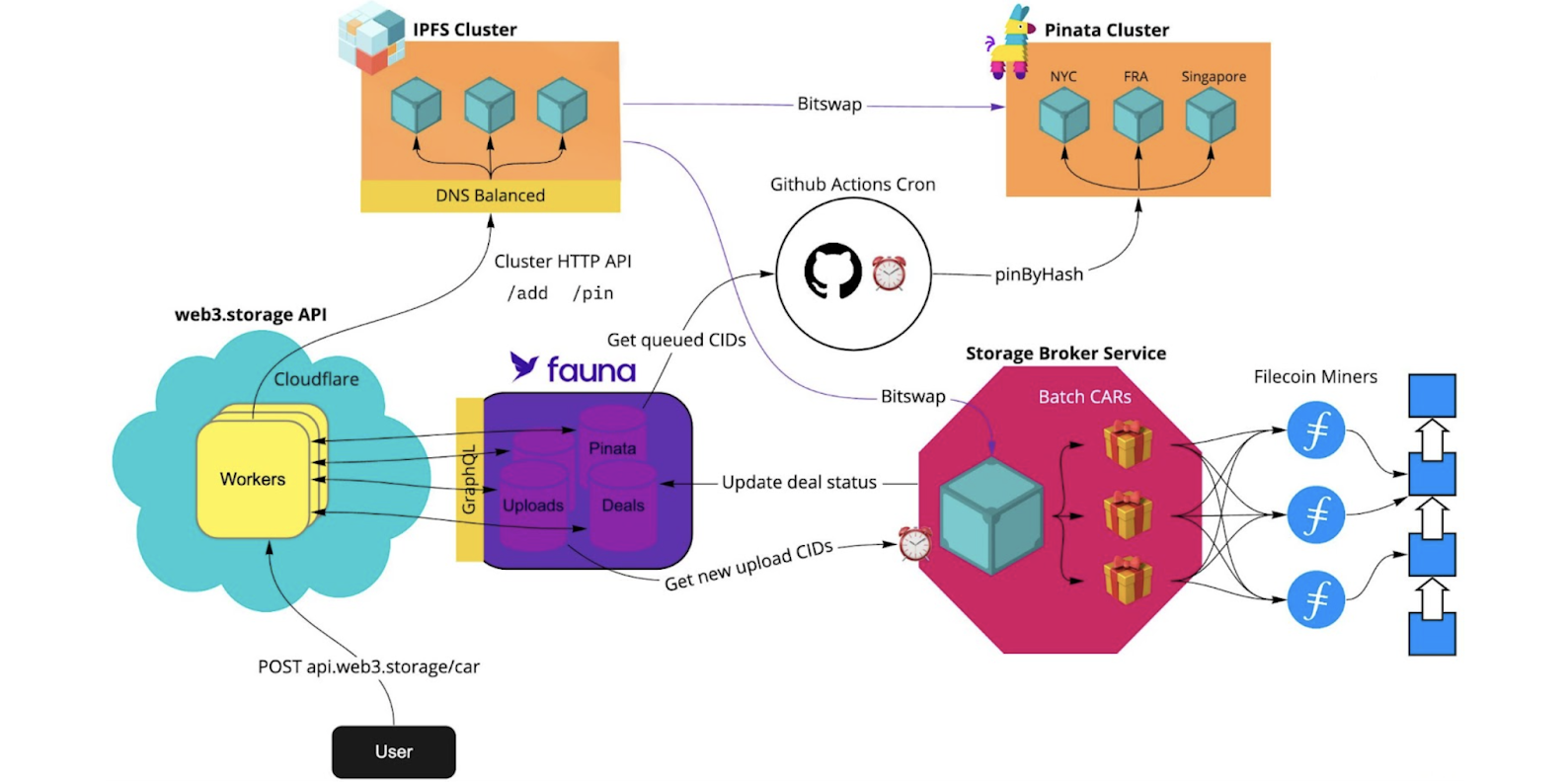
Secure Data Storage: We use highly secure, decentralized storage solutions with multi-layered encryption and robust access control policies. Systems are configured to prevent unauthorized access, and role-based access controls, combined with regular audits, ensure compliance with security policies.
3. Access Control and Authentication
Ensuring that only authorized users can access sensitive resources is fundamental to ACF’s security framework.
Token-based Authentication: ACF uses JWT (JSON Web Tokens) for user authentication. Each time a user logs in or accesses restricted resources, they must provide a valid token, which verifies their identity. This token is securely stored and transmitted over encrypted channels, ensuring that unauthorized access is prevented.
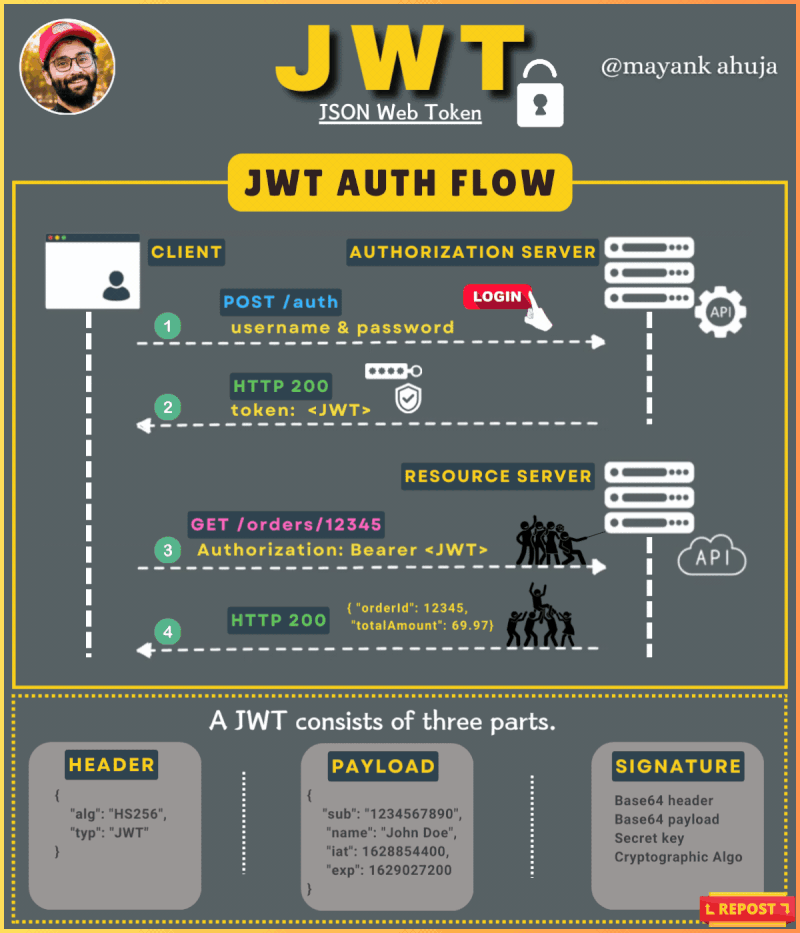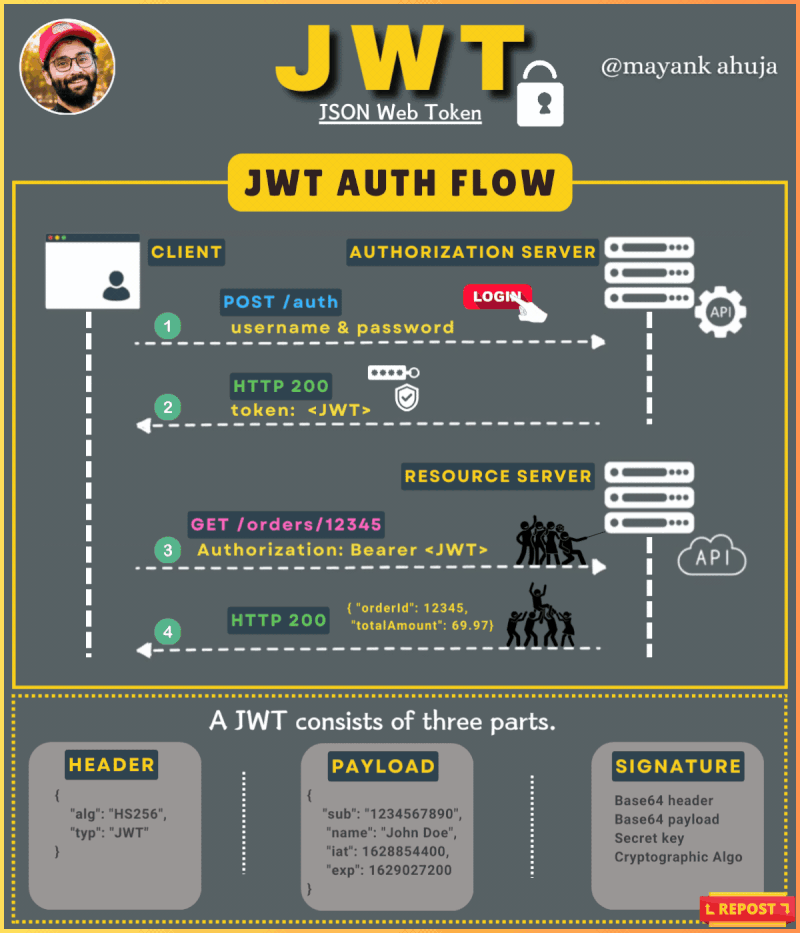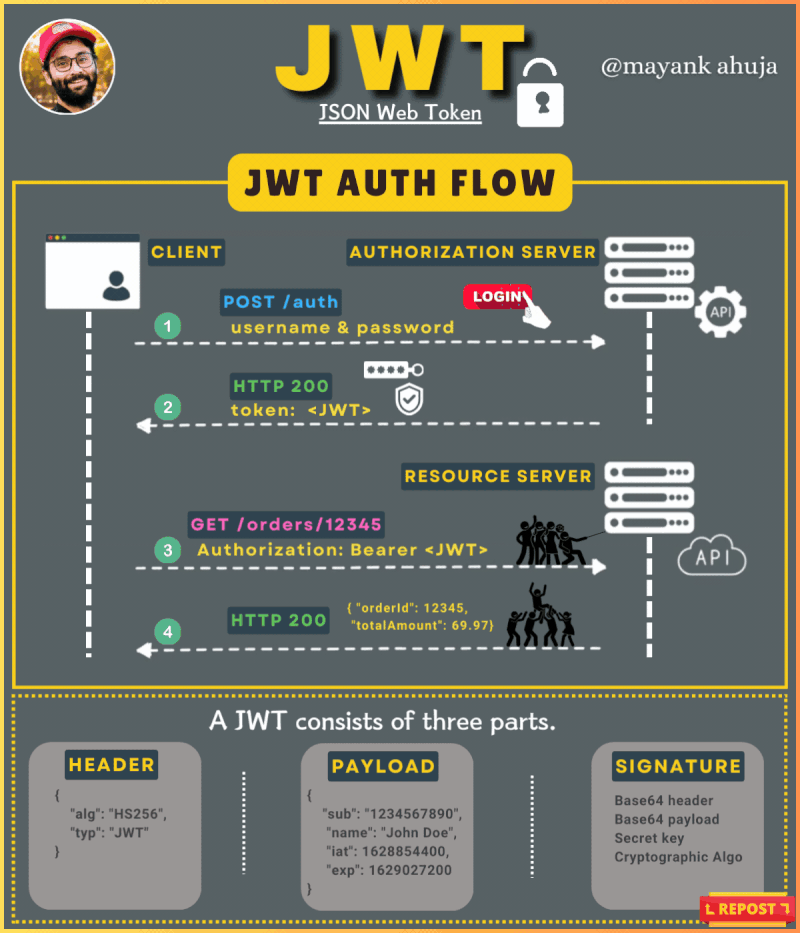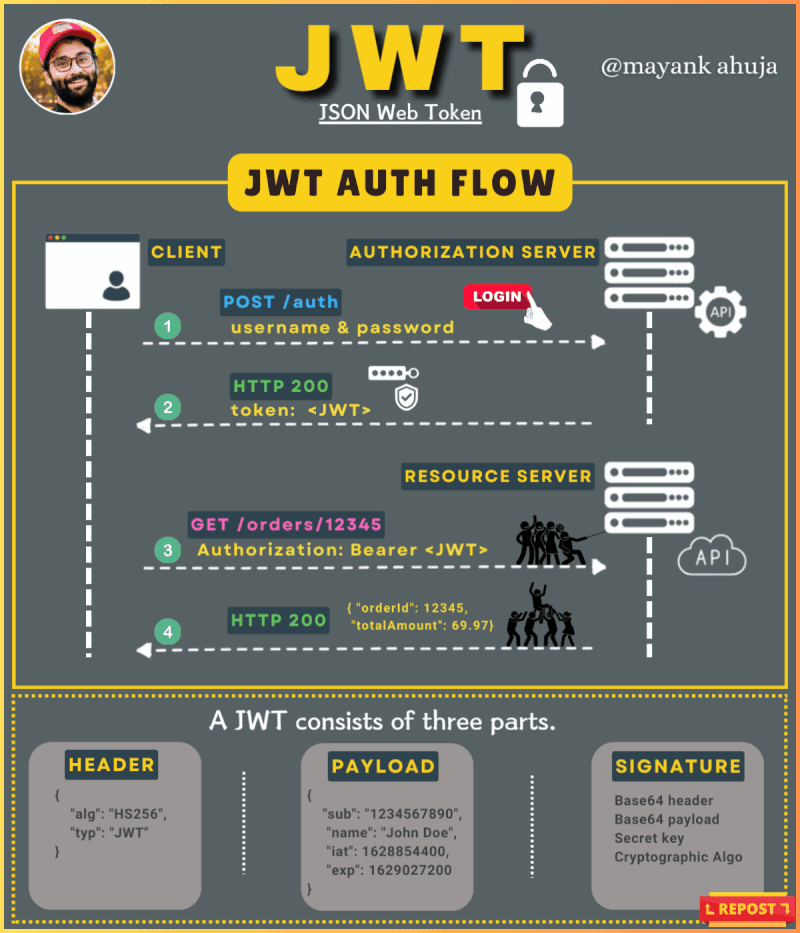
Role-based Access: The system utilizes a role-based access control (RBAC) model, ensuring that each user can only access resources relevant to their role. This minimizes exposure to sensitive data and ensures that only authorized personnel can access critical information.
4. Additional Layers of Security
Rate Limiting & DDoS Protection: To safeguard against brute force attacks, ACF employs rate limiting and DDoS protection measures to ensure the stability and security of the platform.
SQL Injection Protection: Our security infrastructure includes strong safeguards to prevent SQL injection attacks, ensuring that our databases are immune to unauthorized data access.